Digital Assets & Tokenization
Blockchain education and implementation to digitize ownership and document provenance with authenticity, traceability, and legal compliance.
What you’ll get
- Executive education on blockchain use cases & limits — When to use ledgers, tokenization, and smart contracts (and when not to).
- Crypto education (how-to) — Wallets & custody, exchanges and on/off-ramps, security hygiene, risk management, tax-aware tracking, and portfolio construction basics. (Educational only — not financial advice.)
- Provenance / registry patterns with off-chain storage — Hash anchoring, chain-of-custody, and verifiable records for documents and assets.
- Compliance-first workflows & governance — KYC/AML considerations, policies, segregation of duties, and audit trails.
- Security architecture — Key management, multisig/HSM options, access controls, and incident response playbooks.
- Implementation blueprint & pilot — Roadmap, timeline, KPIs, and cost model to move from proof-of-concept to adoption.
Outcomes
- Trusted records and simpler audits.
- Reduced fraud/dispute risk and faster verification.
- Maintainable, compliant operating procedures.
- Upskilled leaders and teams on blockchain and crypto fundamentals.
Credibility note: Our training is grounded in real-world results, including personal experience turning a $2,500 crypto investment into a seven-figure portfolio over time — achieved through disciplined strategy, research, and risk management. Results vary and this is not financial advice.

Case — Digital Document Provenance
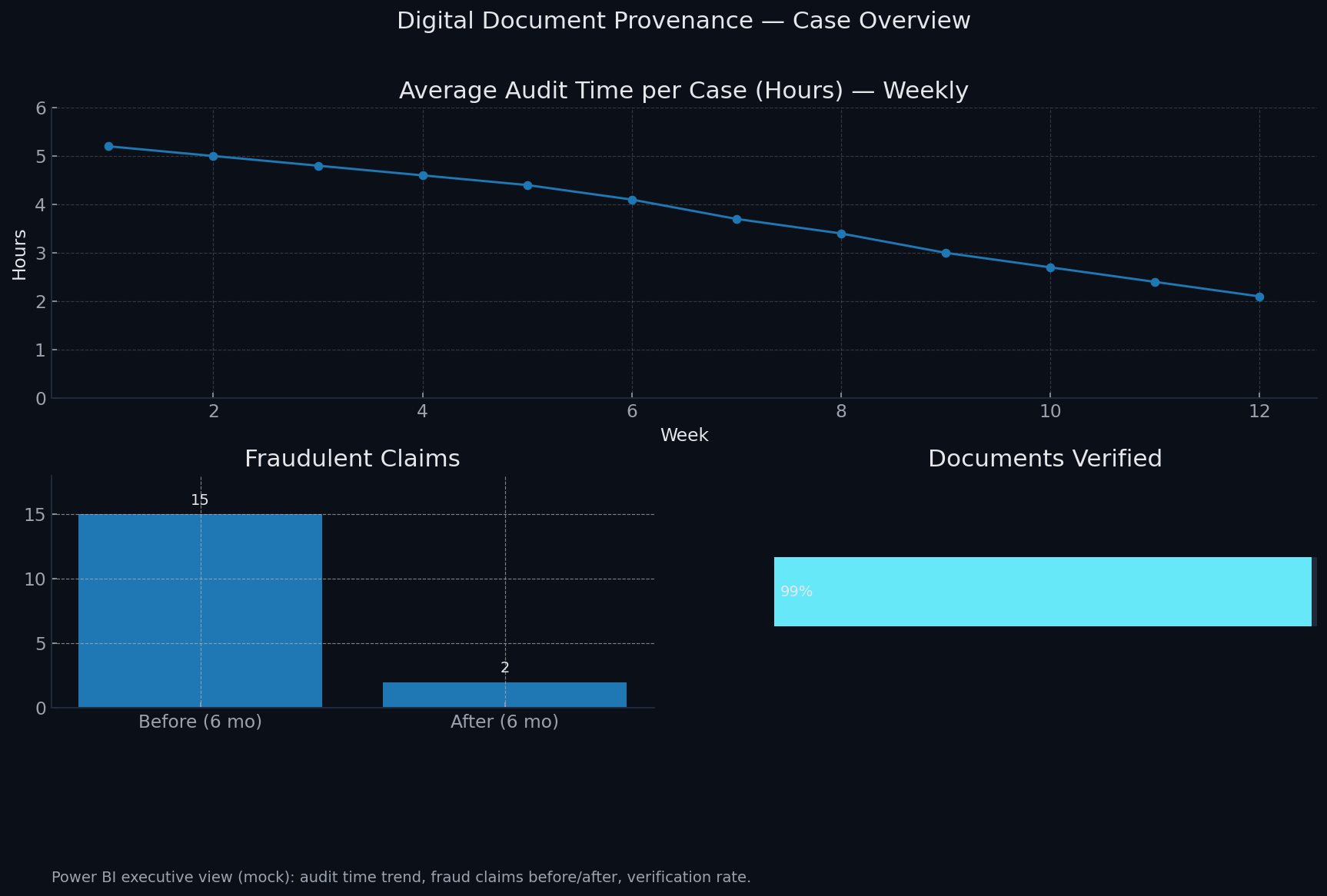
A mid-size law firm faced costly discovery delays and disputes over document integrity. We implemented a compliance-first registry that anchors file hashes on chain and tracks chain-of-custody end-to-end, with a Power BI layer for verification and audit analytics.
- Audit time: reduced by 60% (from ~5 hrs/case to <2 hrs).
- Fraudulent claims: from 15 in the prior 6-month period to 2 after go-live.
- Verification rate: 99% of documents validated via hash match.
What we implemented
- Registry + hash anchoring — SHA-256 fingerprints for each document; immutable proof of existence.
- Chain-of-custody — Ownership, timestamps, and events tracked from intake to final filing.
- Data pipeline to BI — Indexer writes events/metadata to SQL for DirectQuery dashboards.
- Governance & guardrails — KYC/AML considerations, access control, and audit logs.